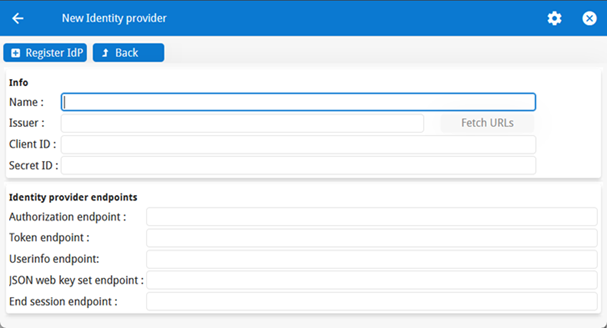
Configure external IdP authentication
Set up GIP to delegate authentication to an external Identity Provider (IdP) while continuing to manage user authorizations.
Before proceeding, register an application with the external Identity Provider (for example: Azure AD, Google, or Okta) and record the Issuer URL, Client ID, and Client Secret. These values will be required during the following configuration steps. Registration steps with IdPs vary by provider; consult the external IdP's documentation for instructions on creating an application and retrieving these values.
The GIP sign-in page will now display an option for users to select and authenticate with the registered Identity Provider.
Users will first have to request a delegated account using their credentials from the external IdP, wait for the GIP administrator to validate it, and only then will they be able to authenticate using the external IdP.