Manage user account requests
You can manage user account requests in the Console App using the dedicated menu for user requests.
When a user submits an account request—for either GIP or an external Identity Providers (IdPs)—the request is saved in the GIP database and appears in the Console App when you log in as an administrator. To manage these requests, use the menu.
Activate the user account request feature
The user account request feature is not enabled by default. To activate it, you must set the
OIDC.account.create.allow parameter to true in the fglprofile configuration file for GIP.
Once activated, users will see the Create Account option on the Console App login screen, allowing them to submit account requests. For step-by-step instructions, see Configure the account request feature.
Required permissions
To manage user account requests, you must be an administrator and have the appropriate scopes assigned in the Console App. The User request menu will only appear if account request functionality is enabled by you as the administrator.
View and manage account requests
In the User request lists screen, account requests are shown in two panes:
- Top pane: pending requests for GIP-managed accounts.
- Bottom pane: pending requests from external IdPs — users who requested an account from an external IdP.
Each request shows login, email, request date.
- Validate (✓): create the user in the GIP database. External IdP requests create a federated user linked to the IdP and its user ID.
- Reject (X): decline the request.
External IdP responses:
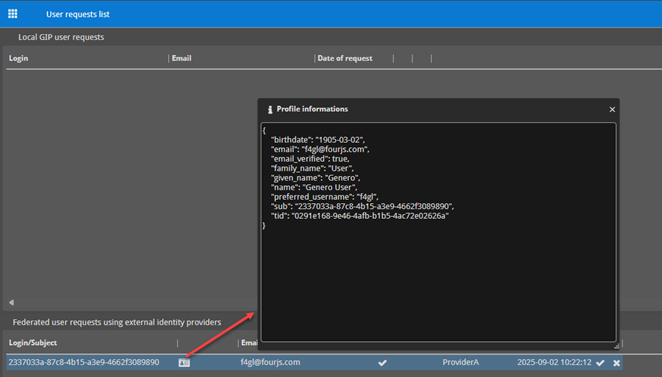
- Profile information dialog: Shows an example of the raw JSON returned by the external IdP’s userinfo endpoint.
- Verified email: Email with a tick mark (✓) indicates the IdP has confirmed the address.
After validation, manage the user (profile, permissions, group membership) as described in Manage users. For federated users you can assign roles and update profile fields, but you cannot manage their password — authentication is handled by the external IdP.