Security levels
The security level determines what verification occurs when a connection arrives on a listening port.
In previous versions, the Genero Desktop Client accepted all connections that arrived on the listening port, without any verification. With Genero 2.0, the security level was raised to level 2.
Change the security level using the gdc -A command line or on the Security tab.
| Security Level | Description |
|---|---|
| 0 | Security level 0 is the least secure. Command Line: Any connection started by the runtime system is authorized. No security message displays. |
| 1 | Security level 1 displays a warning. Command Line: When the runtime system starts a connection:
|
| 2 | Security level 2 uses a key mechanism. Important: This only works when using a direct connection shortcut to start an application.
Command
Line:
If the runtime system does not handle this feature, you will not be able to run an application at this security level. |
| 3 | Security level 3 uses a key mechanism. Command Line:
gdc -A 3Important: This only works when using a direct connection shortcut to start an application.
If the runtime system does not handle this feature, you will not be able to run an application at this security level. |
The security key mechanism check
How the key mechanism works:
- When the GDC starts, it generates two random keys. These are known as UUIDs.
- When the GDC starts a direct connection and that connection uses one of the
@FGLtags (@FGL,@FGLNT,@FGLCSH, or@FGLKSH) in the command, _FGLFEID and _FGLFEID2 are exported. At this point, fglrun has two variables in its environment (_FGLFEID and _FGLFEID2) that it will use to verify the GDC it attempts to connect to. - The GDC gets the _FGLFEID from the DVM via the GUI connection and compares it to the _FGLFEID it initially generated. If they match, it knows that it is connecting to the correct DVM. Otherwise, it should reject the connection.
- The DVM gets the _FGLFEID2 from the GDC. If it matches the _FGLFEID2 value set in its environment, it knows it has the correct GDC. Otherwise, it should reject the connection.
When a check fails, the security level ultimately determines whether to reject the connection or to allow the end-user to override and accept the connection.
The Security Connection Message dialog
When displayed, the Security Connection Message dialog allows a user to accept a connection despite not passing the security checks involving key mechanism verification or hosts.xml validation.
Figure: Security Connection Message dialog
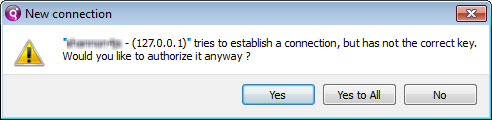
| Action | Description |
|---|---|
| Yes | Accept this connection and only this connection. The connection information is stored in memory for the duration of the connection. Any additional connection from the same host causes the message to be displayed again. |
| Yes to All | The GDC accepts this connection and any other connection from the same host. This setting is
saved to $AppDataDir/hosts.xml when the GDC closes. Tip: You can modify the hosts.xml file if needed, or remove it to
clear the authorized list.
|
| No | The GDC rejects this connection and the application will not run. Tip: Did you
answer "No" by accident? When you next execute the same application, the dialog
redisplays.
|