Genero Identity Provider scenario
This scenario provides an overview of the process for securing applications and web services resources with the Genero Identity Provider (GIP).
ABC Farmers is implementing a system to help them sell apples and oranges. They have written a web service to manage their sales of fruit. Access to the web service is provided by a browser-based application, to be made available to all ABC Farmers customers, workers, and managers. This scenario takes you through the process of securing both the web service and the application, while setting up access for users based on their roles (customer, worker, or manager).
Create the groups
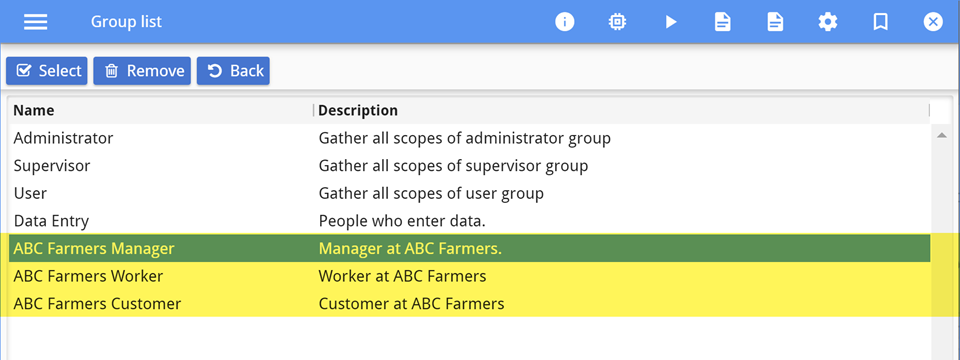
It is more efficient to secure an application for a group of users than on a user-by-user basis. Towards this end, the administrator starts by creating user groups based on the different roles, as shown in Figure 1.
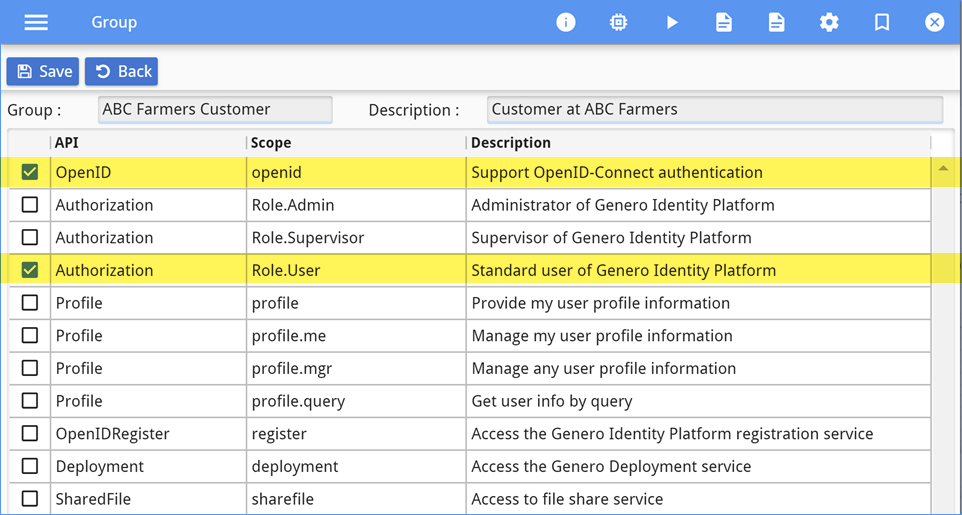
For each group, the administrator selects the authorization role of Role.User
(for the Authorization API), as each member of these groups is a "standard user of
Genero Identity Platform". In addition, the default scope openid (for the
OpenID API) is kept, as it is required for the Genero Identity Provider and single
sign-on. Figure 2 shows the
initial scopes selected for the ABC Farmers Customer group; the scopes for the Worker and Manager
groups would be identical at this stage.
Secure the web service
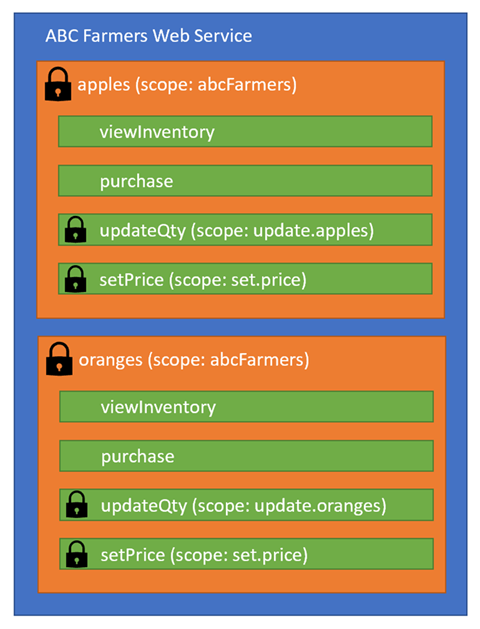
With the groups created, the administrator continues to secure the web service.
- Customers can find out what fruit is available and purchase the fruit.
- Farm workers can update the inventory when new produce arrives.
- Farm managers can set prices.
Secure the application
Role.User. A user must have the Role.User role to access the
application.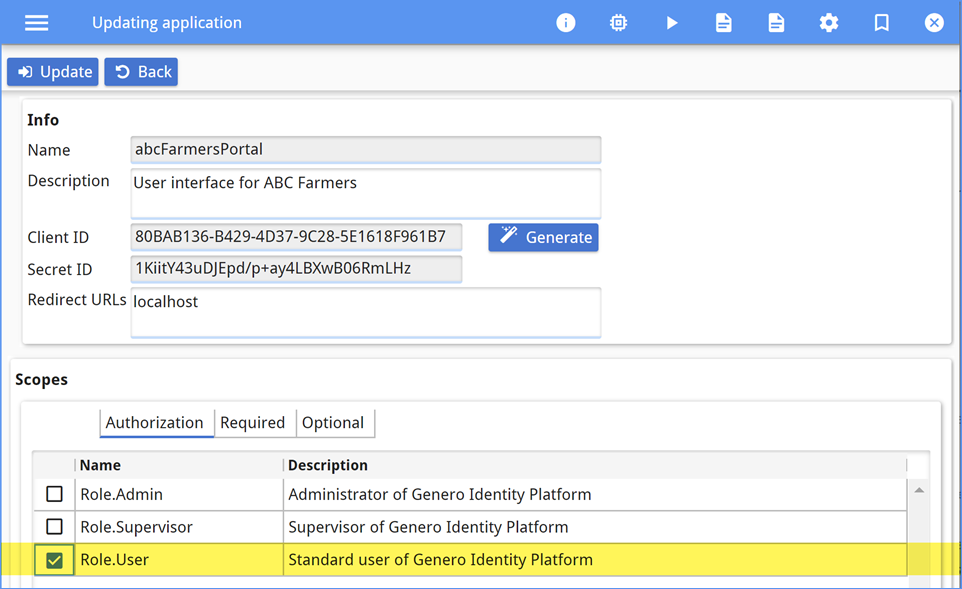
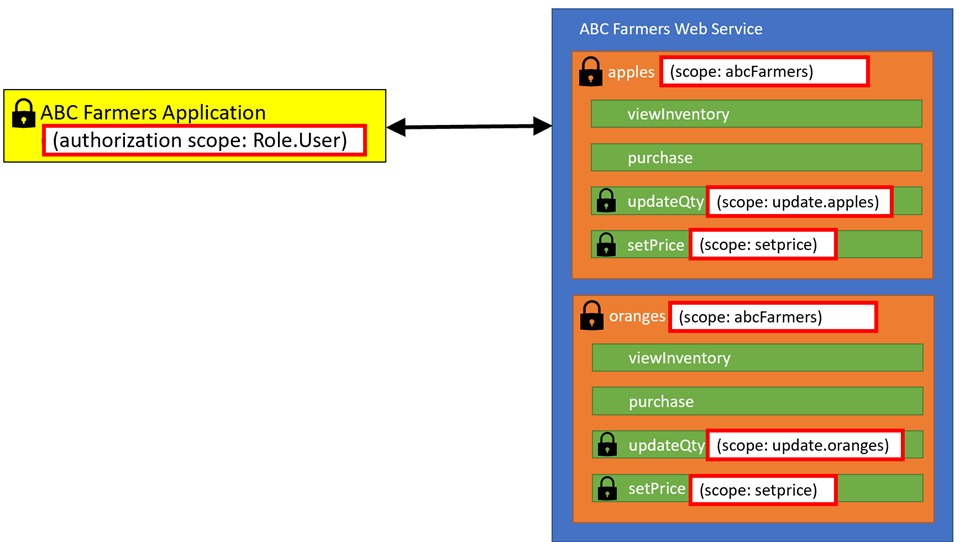
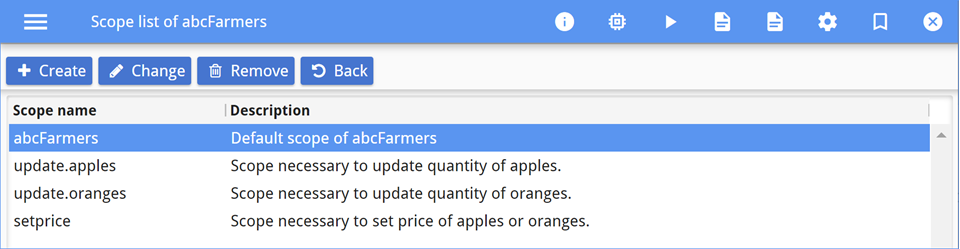
The administrator must determine which scopes are required and which are optional. For the ABC
Farmers web service, if a user does not have the abcFarmers scope, they will not be
able to access any of the resources or operations. Customers, however, will not need the
update.apples, update.oranges, or setprice
scopes. Based on this analysis, the administrator sets the required and optional scopes for the ABC
Farmers Portal application, as shown in Figure 7 and Figure 8.
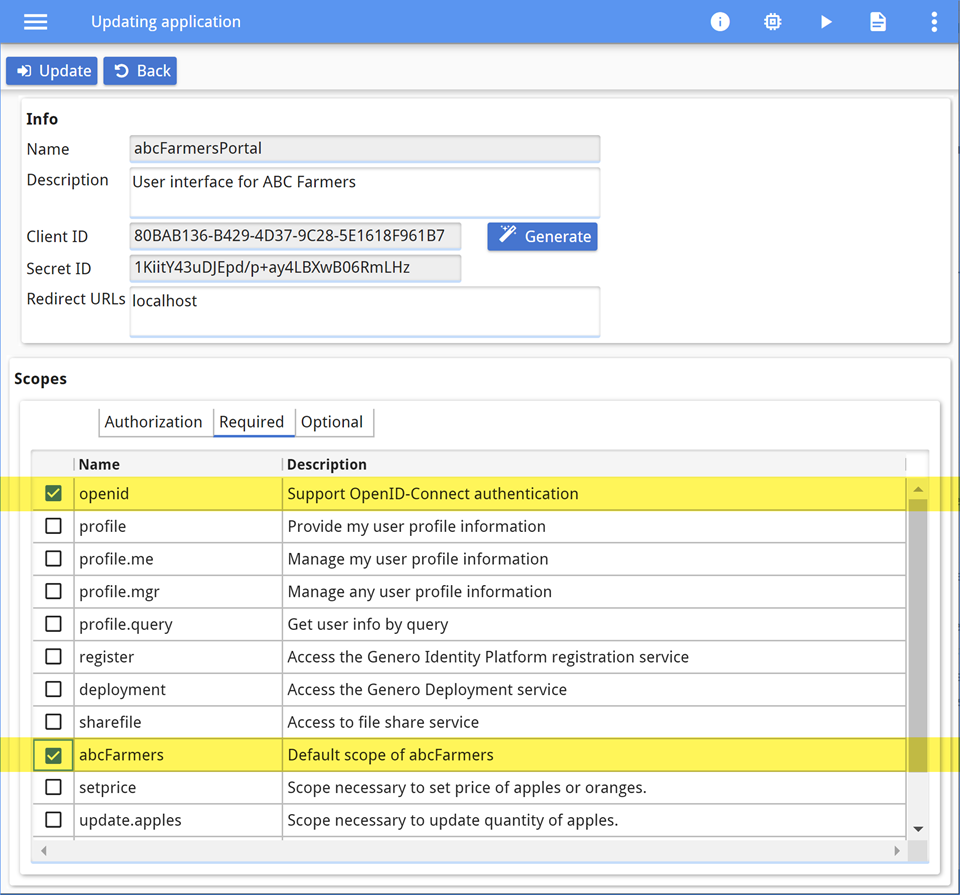
Users without the abcFarmers scope will not be allowed to start the application,
as it is a minimum scope requirement. The openid scope is required for
authentication purposes.
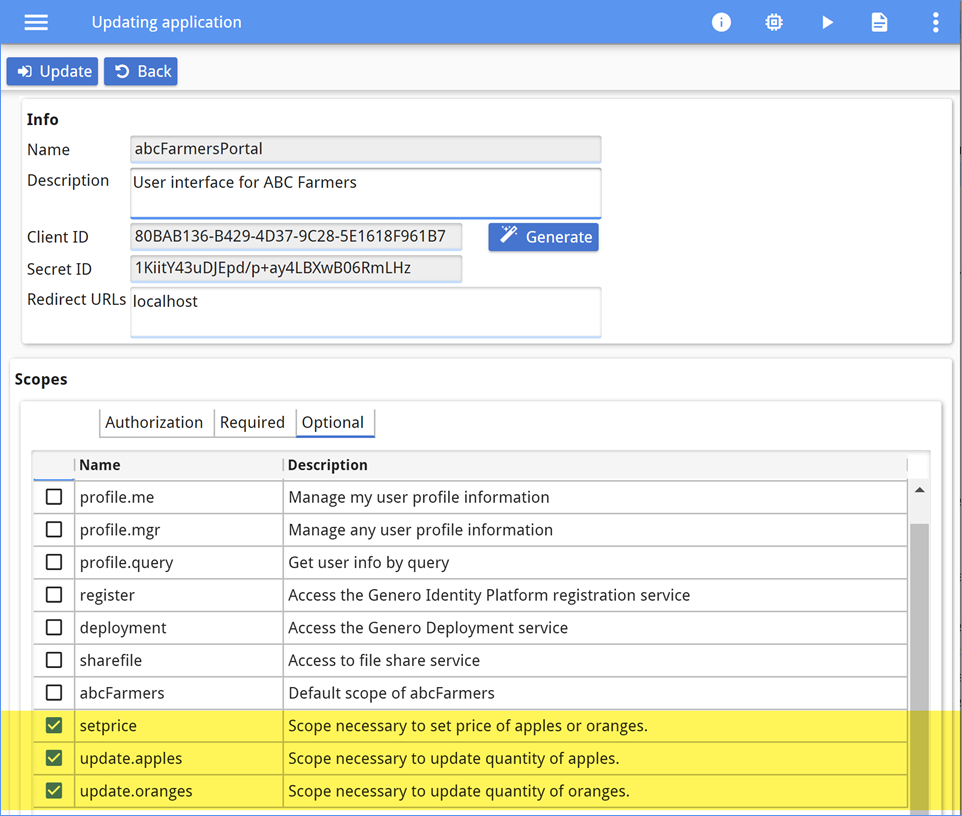
Users without the optional scopes will still be allowed to start the application, however they will not be able to access the operations protected by those scopes.
Set scopes for groups
The administrator has defined the user groups, registered the scopes for the web service, and secured the browser-based ABC Farmers Portal application. Next, the administrator selects the scopes for each group.
abcFarmers scope to access the resources. This scope is
added to the ABC Farmers Customer group, as shown in Figure 9.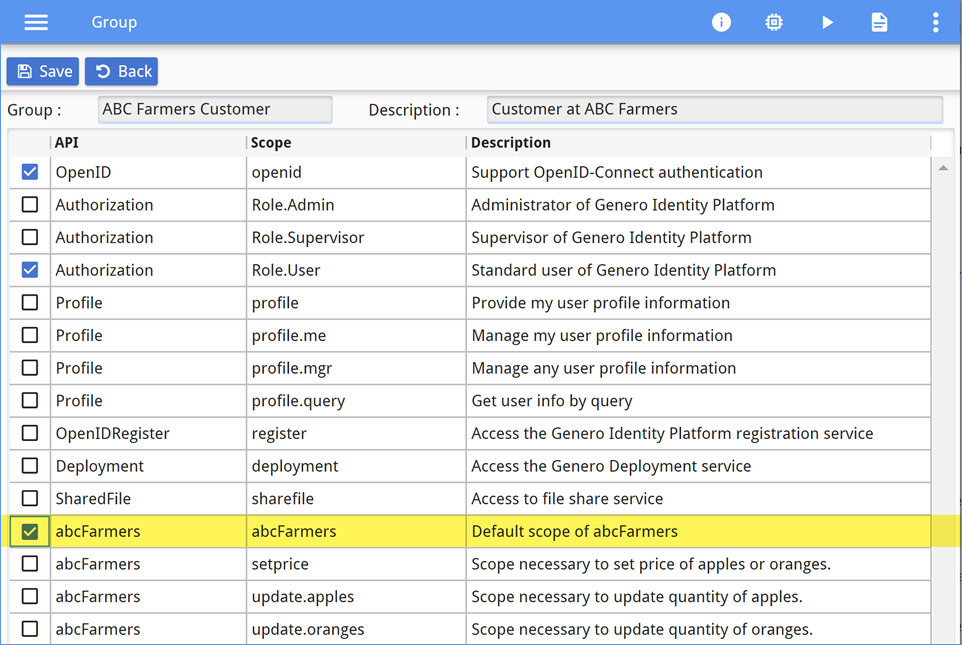
abcFarmers scope to access the resources. In addition,
the worker needs the update.apples and update.oranges scopes to
update the inventory of oranges and apples as new shipments arrive. These scopes are added to the
ABC Farmers Worker group, as shown in Figure 10.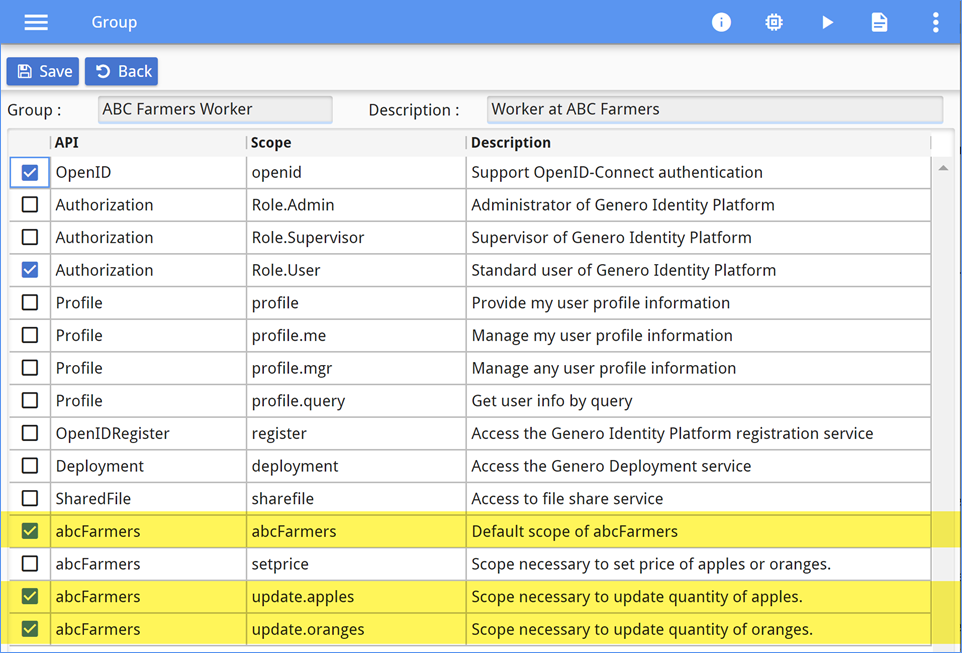
abcFarmers scope to access the resources. In
addition, the manager needs the setprice scope to update the prices of apples and
oranges. These scopes are added to the ABC Farmers Manager group, as shown in Figure 11.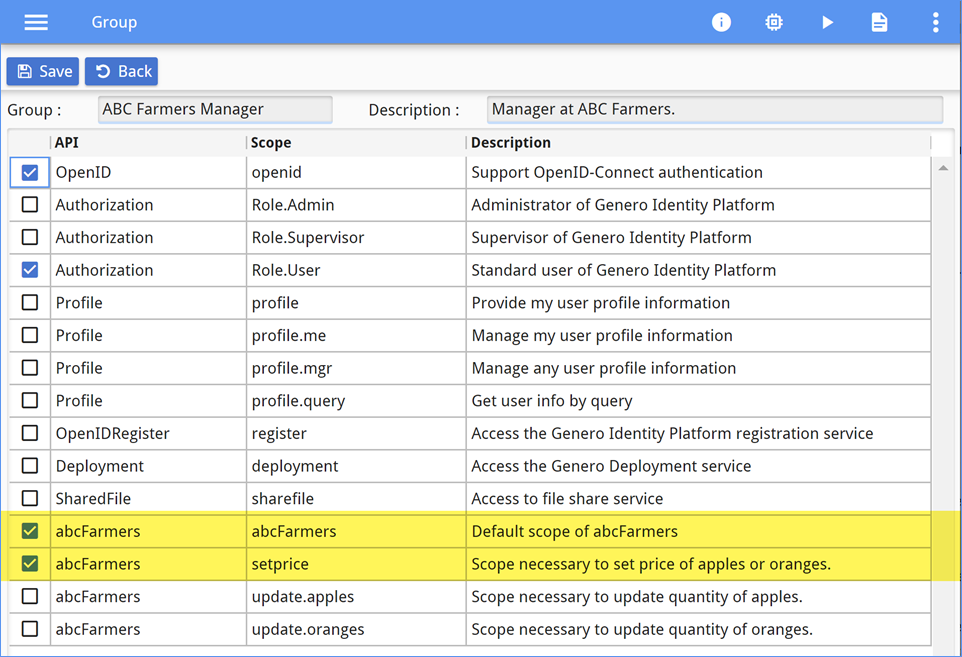
The scopes for each of the three groups are set.
Assign groups to users
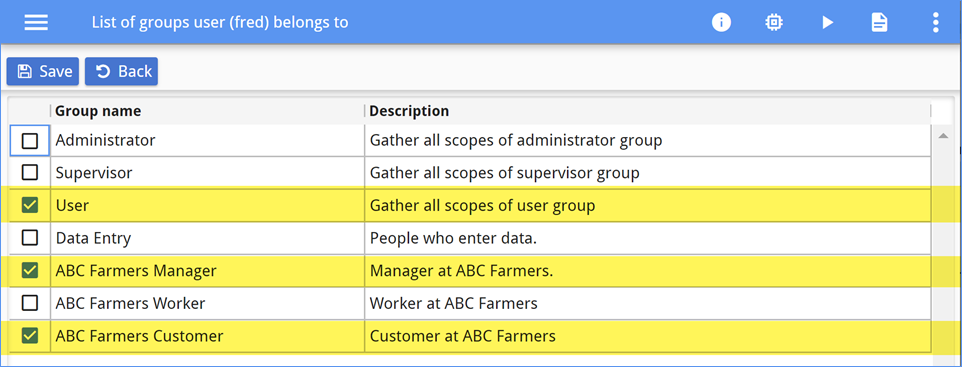
The user inherits the scopes assigned to the groups in which they belong. In the Console App interface, scopes inherited by group membership display as selected but with a faded gray font, as shown in Figure 13.
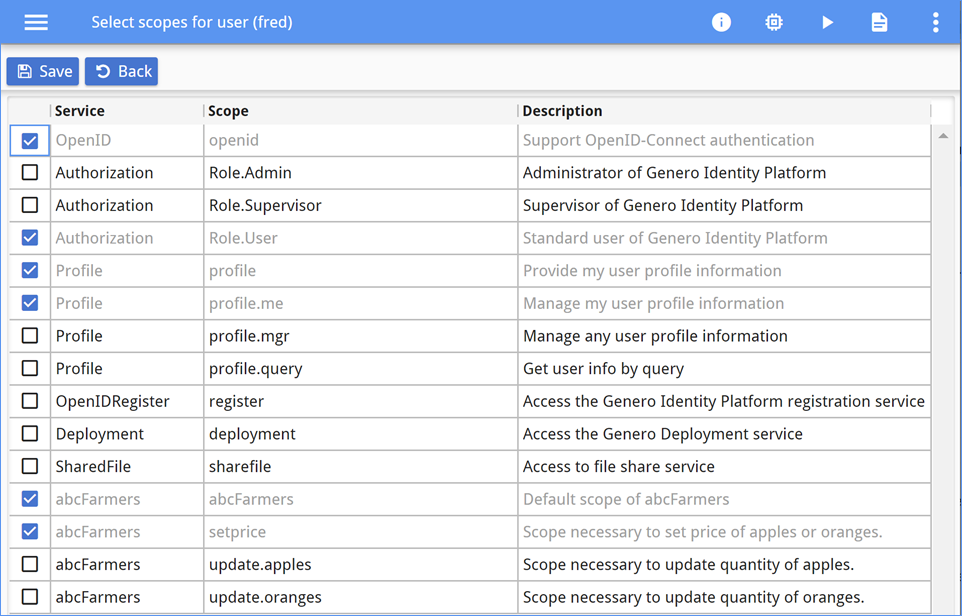
If groups are used well, there should never be a need to select roles or scopes directly for a user. When a new user is registered with the Genero Identity Provider, the administrator only needs to select which groups are a match for that user, and user setup is complete.
Secure a service (script) application
The ABC Farmers managers do not always want to log in to the application to update pricing; they have already entered prices into another system. An application – a back-end service with no user interface – has been created to update the pricing of fruit based on data pulled from other systems. The script is scheduled to run daily. The script will need access to the secured web service to complete the pricing updates.
abcFarmers scope required to access the resources and the
setprice scope required to access the operation to update the prices. These scopes
are added to the service, as shown in Figure 14.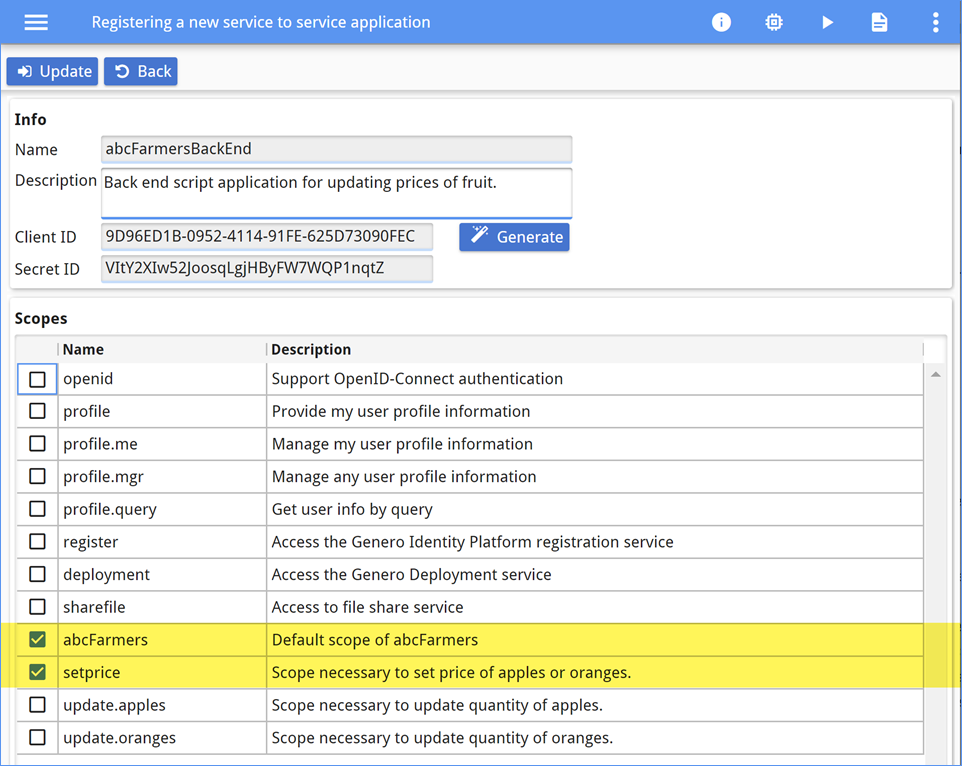
Now, the script will be able to use the GetToken tool to retrieve an access
token to be used to update the prices, as it has the required scopes.
Scenario summary
- Securing applications and RESTful web services.
- Managing users and groups.