GDC and SSH overview
GDC with SSH provides security and port forwarding.
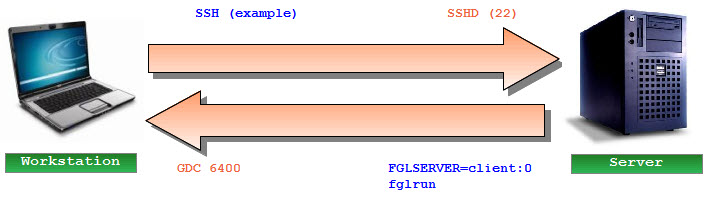
SSH stands for "Secure SHell". It was designed to replace the 'r' commands like rlogin and rsh, because they offer no real security. SSH encrypts all data end-to-end, offers data compression, and prevents snooping and connection hijacking. One additional feature it offers is port forwarding.
Port forwarding allows an application on one computer to connect to a local port and have its data tunneled through an SSH session to the other computer. This does not require you to open any ports on your firewall router, other than the port you already have open for SSH. This is a distinct advantage. If you have firewalls, this is advantageous as Genero needs to establish a connection from the client to the server to start the user application, and another connection originating from the user application to the client to display the graphical user interface. When Genero establishes a connection from the server to the client, it can use the existing connection to tunnel the graphical connection.
Any environment that uses firewalls or connections over the Internet should use SSH, SSH2 or HTTPS for those connections. Furthermore, any production environment on an intranet or internet should use a secured layer. You should never send unencrypted data such as account numbers, social security numbers, and passwords through the Internet. Some companies might even consider using secure shell connections for internal use when handling sensitive data such as accounting and payroll information. At any point along the way, someone could be monitoring the data, for network diagnostics or possibly with malicious intent. Whatever the reason, encryption is simple and offers peace of mind.
SSH is comprised of two main components, the server component "sshd" and the client component "ssh". Genero provides its own client component (built-in).