Genero Identity Platform components
Services, applications, and tools work together to secure applications and services and perform Single sign-on (SSO) for applications delivered by a Genero Application Server (GAS).
The Genero Identity Platform is made up of a set of applications and services to handle user authentication; additional components allow you to deploy and secure applications and Web services without having to add authentication logic to your application sources. Figure 1 represents a high level view of the components that make up the Genero Identity Platform.
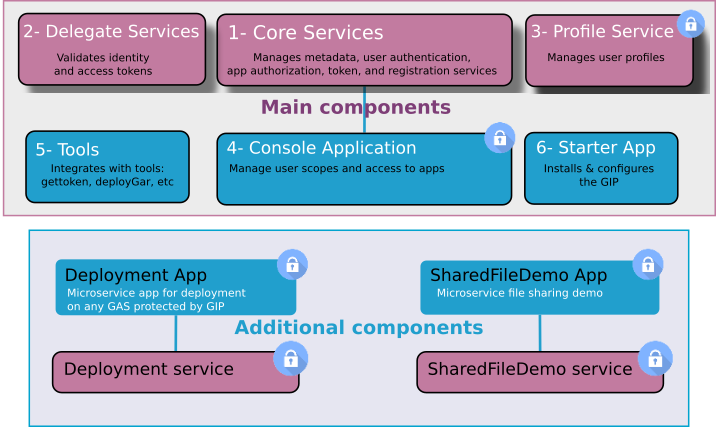
Main components
Passwords are stored in the GIP database as hash values, not as plain text. Hash password storage provides essential security in case your database is stolen or compromised by a hacker, because a password can not be reverse engineered from a hash.
When a user types the URL of a secure application into a browser, the GIP performs an identity check on the user from a log in. If the user's identity is verified and they are allowed access, the user is redirected to the application.
Some application and service components of the GIP are secured by the GIP and access to them requires user log in. These are shown in Figure 1 with the padlock symbol.
The main components are needed to secure applications and Web services and manage users. They include services, administrative applications, and interoperability with Genero command line tools.
- Core Services (1)
- The core services of the GIP handles:
- User authentication and Single Sign-on (SSO)
- The creation of access tokens and identity tokens
- The registration of applications
- Delegate Services (2)
- The delegate services validate the identity token and access tokens. There are two separate
delegate services that provide each function:
- The OpenIDConnectServiceProvider service manages all SSO delegated requests
for applications. It redirects the start of a Genero application to the GIP and checks the validity
of the identity token returned by the GIP via the callback URL. For more details about the SSO
workflow, see Single sign-on workflow.
This service also provides the application with an access token; the application needs to have the access token when sending an HTTP request to a REST service. The delegate service sets the environment variable (
OIDC_ACCESS_TOKEN) with the access token received from the GIP and starts the application. - The Access delegate service manages all requests between an application and
a REST web service. It decodes the access token, and gets the scope (or list of scopes) from it. It
checks the token's signature and if it is valid, it forwards the access token with the scope (or
scopes) to the REST service. Access is granted if scopes correspond with what is defined in the
WSScopeattribute for access to the resource.For more information on Web service scopes, see the WSScope page in Genero Business Development Language User Guide and Manage Web service access scopes.
- The OpenIDConnectServiceProvider service manages all SSO delegated requests
for applications. It redirects the start of a Genero application to the GIP and checks the validity
of the identity token returned by the GIP via the callback URL. For more details about the SSO
workflow, see Single sign-on workflow.
- Profile Service (3)
- The profile service manages user profiles for SSO. A user profile includes a name, date of birth, phone number, email address, and more. This is a secure service you access through the Console App. The Starter App installs the profile service, or it allows you to specify an alternate profile service.
- Console App (4)
- The Console App provides a secure interface for registering applications and Web services to be secured by the GIP, and managing users and groups. Administrators can also view current tokens, and revoke a token's ability to renew. See Managing GIP components.
- Tools (5)
- The GIP integrates with command line tools such as the GetToken, DeployGar, and DeployGbc services.
- Starter App (6)
- The Starter App is for the initial configuration of the GIP. Run this application once to specify the initial configuration of the GIP. It sets the administrator login and password. See Setting up the Genero Identity Provider.
Additional components
When you install the GIP, you are given the option to install additional microservices and applications.
- Deployment Service
- This microservice can deploy, secure, and manage applications and Web services, and deploy and
manage Genero Browser Client (GBC) customizations. Using the deployment service allows
you to deploy and secure applications and Web services without having to add
authentication logic to your application sources. Install this service on each GAS
where you plan to deploy an application or Web service using the Deployment App. Tip:
The DeployGar and DeployGbc command line tools can also be used with the deployment service. They work with the GetToken tool to get an access token for the service. See Automate application deployment via scripts.
- Deployment App
- This application provides a secure interface to the deployment service. For instructions on using the Deployment App, see Deploying and securing applications and web services.
- SharedFileDemo service
- This microservice can push and share files between users in the system.
- SharedFileDemo app
- This application provides a secure interface to the SharedFileDemo service. You currently must install the service and its corresponding application on the same GAS in order to use the microservice.