Reasons on the security side and on the application server side.
- On the security side, the goal is to create a Single Sign On (SSO) secured environment.
- On the GAS side, the goal is to be able to launch the DVM in the name of User Agent (Web Browser or GDC) user account.
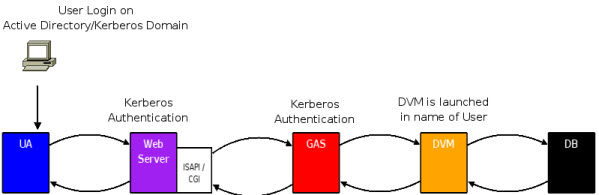
Figure 1. Kerberos Authentication Flow